ICAP Servers
Integrate PrivX with ICAP servers, to provide virus and content scanning for users' connections.
| ICAP Support | |
|---|---|
| Servers | ClamAV McAfee WithSecure Atlant |
| Modes | REQMOD RESPMOD |
| Connection Types | SSH via PrivX GUI SCP via native clients SFTP via native clients RDP via PrivX GUI HTTPS via PrivX GUI |
Enabling ICAP for File Transfers
When ICAP is enabled, all users' file uploads and downloads are scanned. Uploaded files are scanned before they are sent to target hosts; downloads are scanned before they travel from the shared directory to the users' machines. Files that do not comply to corporate policy are blocked.
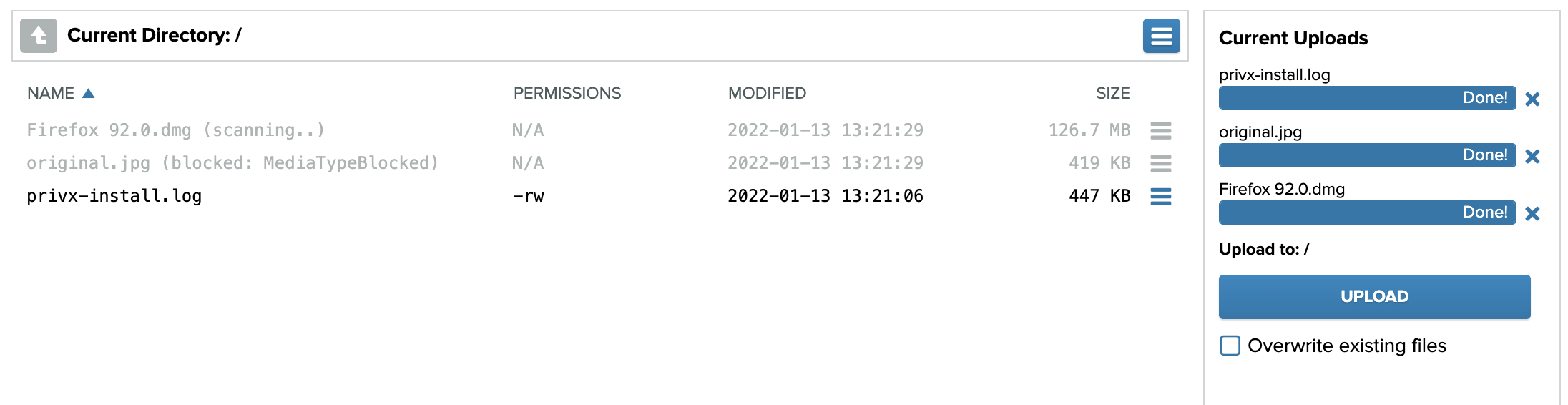
To enable ICAP for file transfers, first ensure that:
- For best performance, we recommend placing the ICAP server close to your PrivX servers (with fast network connection) to speed up file scanning.
- The ICAP-server hostname and port are accessible from all PrivX servers.
To set up ICAP:
-
Access the PrivX GUI. On Administration→Settings→Global under ICAP, provide your ICAP settings:
- Enable file-transfer scans for desired connection types.
Note that the setting for web-based RDP also applies to HTTPS file transfers. - Provide the ICAP-server host name and port.
- Provide either ICAP RESPMOD URL or ICAP REQMOD URL (depending on whether your ICAP server uses response modification or request modification). You should verify the correct URL from your ICAP-server configuration.
- ICAP service name is an optional attribute, required by some servers (example value: squidclamav).
- Enable file-transfer scans for desired connection types.
-
Restart PrivX to apply your changes.
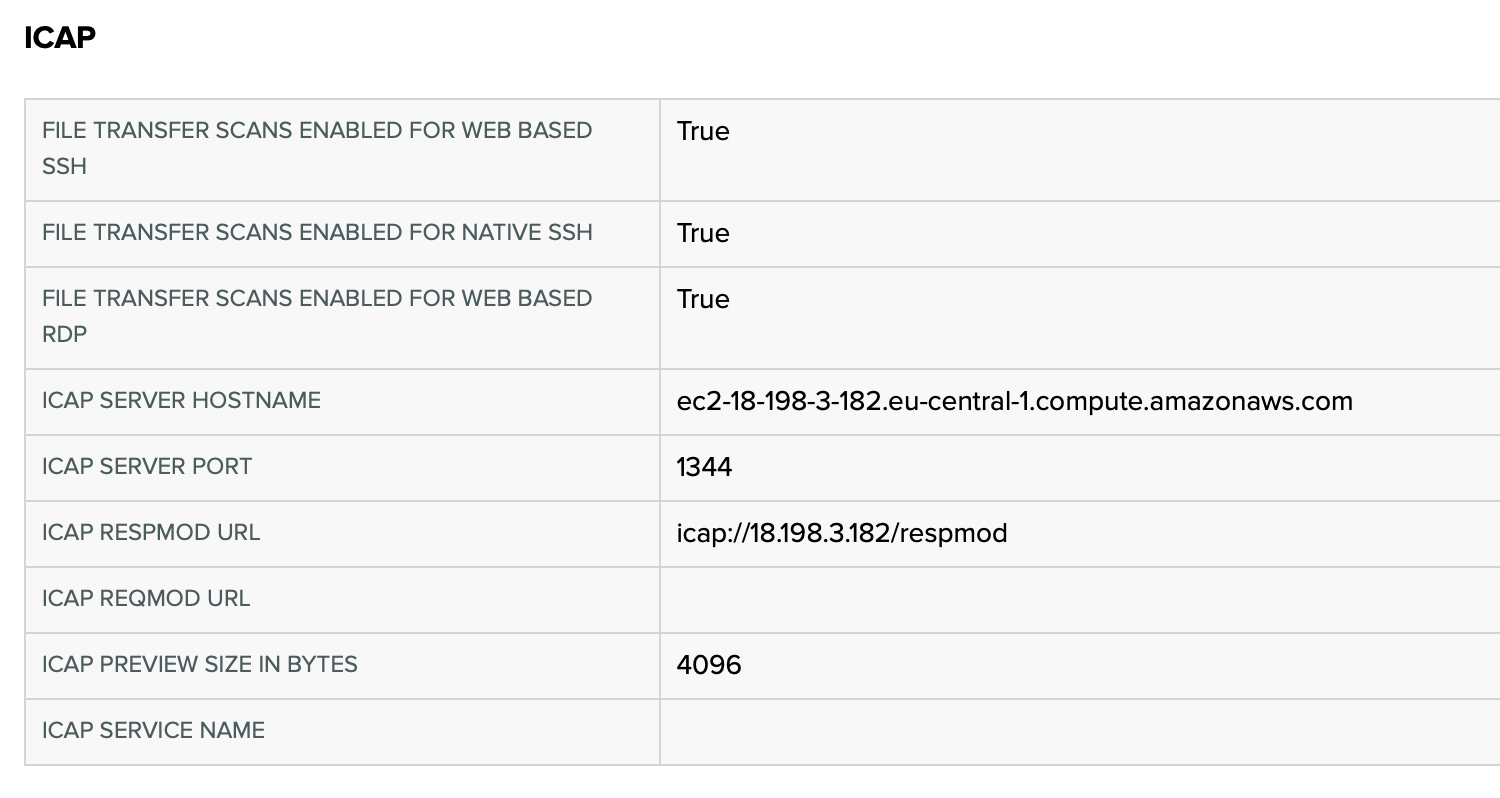
Example ICAP configuration
Enabling ICAP for HTTPS Traffic
To enable ICAP scanning for all HTTPS traffic (instead of just File transfers), repeat the following setup on all PrivX Web Proxies:
-
To allow inspecting traffic for malicious files, add the following lines to
squid.conffile on PrivX Web Proxy:icap_enable on icap_service service_resp respmod_precache bypass=0 icap://10.1.1.5:1344/respmod adaptation_access service_resp allow allSave your changes to the file.
-
Restart the squid service to apply your changes:
systemctl restart squid
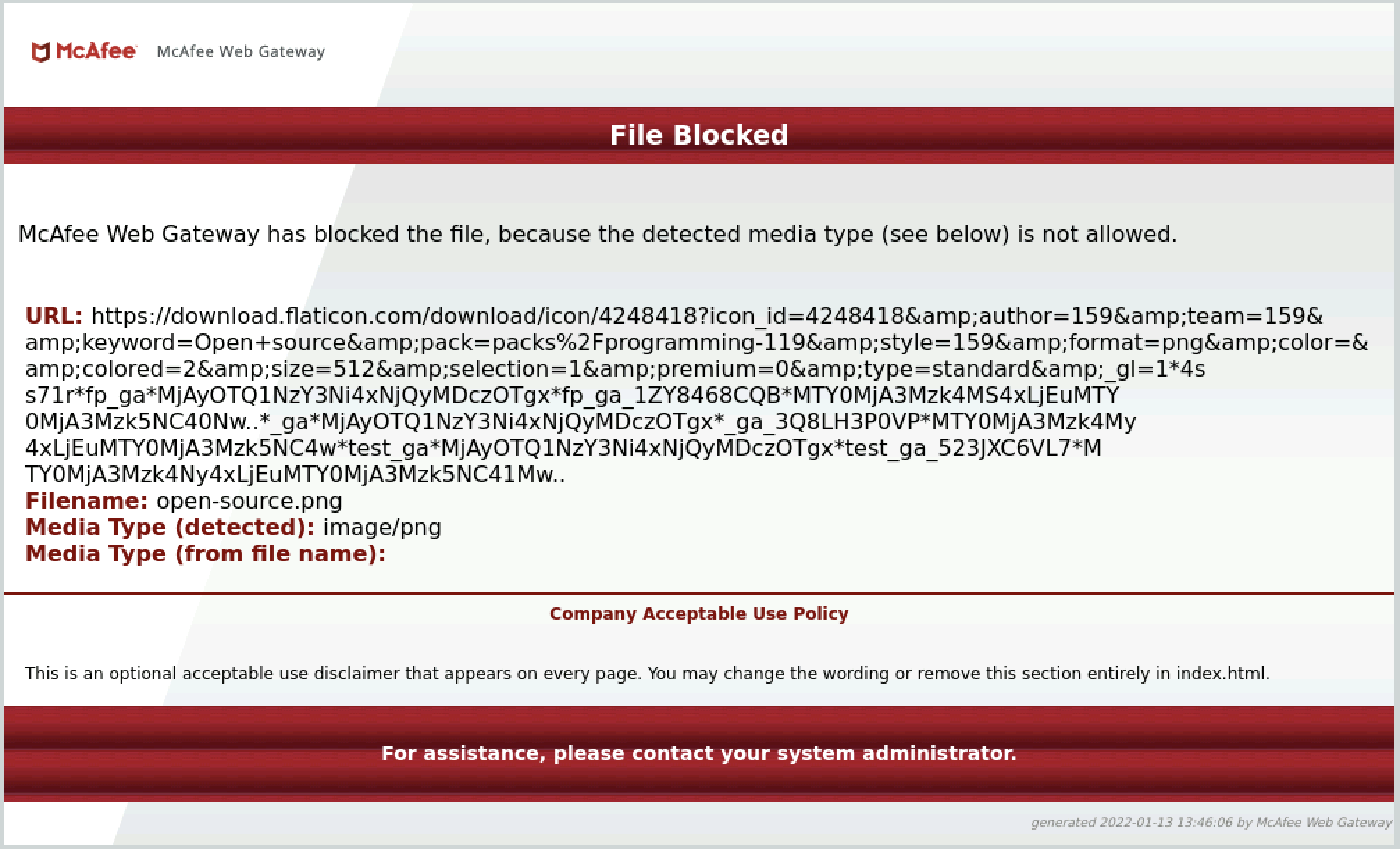
Trying to access blocked content should show an error message on the container browser (example using McAfee):
For more information about ICAP setup with Squid, consult the Squid documentation at http://www.squid-cache.org.
Updated almost 2 years ago
