Deploying PrivX to Google Cloud Platform: architecture blueprint
This document provides information how to deploy PrivX to Google Cloud infrastructure.
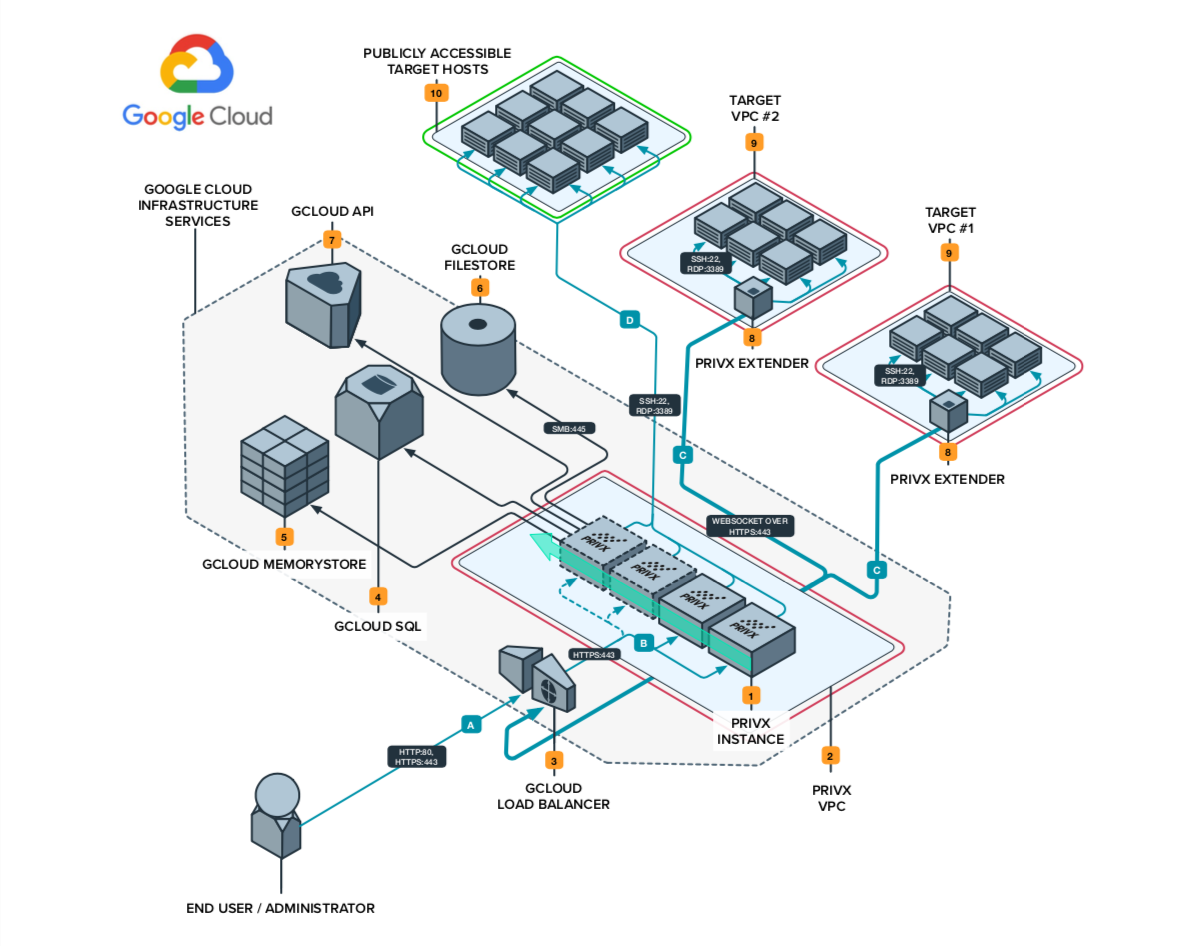
Reference architecture components
- PrivX instance is the host the PrivX service will be running on. A suitable starting point is an instance with 2 VCPU and 4 GB RAM running CentOS7. A minimum of 2 PrivX instances are required for high availability, scalability achieved through deploying additional PrivX instances.
- PrivX VPC will contain the running PrivX instances.
- GCloud Load Balancer distributes traffic for the PrivX instances for HTTP & HTTPS traffic. Session affinity: Cookie must be set.
- GCloud SQL is used for persistence. A suitable starting point is a PostgreSQL database server with 2 VCPUs and 7.5 GB RAM and a 100 GB storage.
- GCloud Memorystore is used for triggering internal content updates - 1 GB (minimum possible) size is sufficient
- GCloud Filestore is used for audit trail storage - premium tier is recommended for read/write throughput, size depends on usage
- GCloud API - if configured to do so, PrivX will index all computing resources from AWS and present them as connectable targets
- PrivX Extender is deployed to a VPC and it establishes a secure websocket control connection back to PrivX. It routes traffic from PrivX to target hosts within the VPC.
- Target VPC is a network containing target hosts which have no publicly accessible addresses
Publicly accessible target hosts can be accessed directly from the PrivX via SSH/RDP in case they have an address the PrivX instance can connect to.
Connections
A. Administrators, end users and API clients will always access PrivX via HTTPS:443. HTTP:80 is required for Windows CRL checks and redirects to HTTPS
B. All PrivX internal communication, including connections from the Application Gateway to application nodes is over HTTPS:443
C. The PrivX Extenders establish secure websocket connections back to PrivX instances - subsequent connections from the Extender to target hosts are done using SSH/RDP
D. PrivX can access target hosts directly via SSH/RDP
Disclaimers
This document includes instructions regarding third-party products by Google. This blueprint is provided for general guidance only.
The architecture in this blueprint was verified against the Google Cloud products current in April 2019. These instructions will need to be adapted when using other versions of Google Cloud products.
SSH Communications Security Corporation does not make any warranties as to the accuracy, reliability, or usefulness of these instructions, or guarantee that the content related to third-party products is up to date.
SSH Communications Security Corporation does not provide any warranties regarding third-party products, such as Google Cloud, nor provide any support or other services for third- party products.
For instructions about setting up and operating Google Cloud products, we always recommend that you consult the official Google Cloud documentation intended for the specific version(s) of Google Cloud products in your use, and/or directly contact Google Cloud representatives or support.
Updated over 3 years ago
