Microsoft Azure AD as User Directory via LDAPS
This document provides instructions for adding users from Azure Active Directory (Azure AD) as PrivX users. By following these instructions, you can allow users from your Azure AD to log into PrivX. Such users may then be granted SSH/RDP access similarly to regular AD users.
This version of the instructions is suitable for Azure environments with LDAPS. For azure environments without LDAPS support, consider checking Microsoft Azure AD as user directory via graph API instead.
Disclaimers
This document includes instructions regarding third-party products by Microsoft. These instructions are provided for general guidance only.
Documentation involving third-party products include configuring applications in Microsoft Azure. The instructions in this manual were verified against the Microsoft Azure version that was current in June 2018. These instructions will need to be adapted when using other versions of Microsoft Azure.
SSH Communications Security Corporation does not make any warranties as to the accuracy, reliability, or usefulness of these instructions, or guarantee that the content related to third-party products is up to date.
SSH Communications Security Corporation does not provide any warranties regarding third-party products, such as Microsoft Azure, nor provide any support or other services for third- party products.
For instructions about setting up and operating Microsoft Azure products, we always recommend that you consult the official Microsoft documentation intended for the specific version(s) of Microsoft products in your use and/or directly contact Microsoft representatives or support.
It is always your responsibility to define the final production setup for the Microsoft products that you use.
Prerequisites
Check and ensure the following before performing the procedures in this document:
- Your Azure AD must contain the users that are to access PrivX.
- Enable LDAPS for your Azure domain. For more information about doing this, see Microsoft Azure documentation at:
https://docs.microsoft.com/en-us/azure/active-directory-domain-services/active-directory-ds-admin-guide-configure-secure-ldap - To allow PrivX to detect users on Azure AD, obtain the following bind data from your Azure AD:
- Bind-user credentials (distinguished name and password).
- Base DN for searching users.
- Name of the LDAP field containing the users' login names (typically userPrincipalName).
- For configuring PrivX servers, obtain the following data regarding your Azure deployment:
- root-CA certificate of your Azure domain (in PEM or DER format).
- Your Azure AD public URL.
- The Directory ID of your Azure AD.
- You will need access to your Azure Portal with sufficient permissions for registering new apps.
- You must be able to perform terminal commands as root on your PrivX servers.
- You will need access to PrivX as a privx-admin.
Integration Steps
The high-level workflow for allowing Azure AD users to log into PrivX involves:
- Registering PrivX in Azure.
- Adding Azure-AD Users to PrivX.
These steps are described in more detail in the following sections.
Registering PrivX in Azure
Azure AD users use Microsoft login for authenticating to PrivX. To enable this functionality, you must first register PrivX as an app in Azure:
-
Log into Azure Portal at https://portal.azure.com/
-
In the Azure Portal, navigate to Azure Active Directory→App registrations, then click New Application Registration.
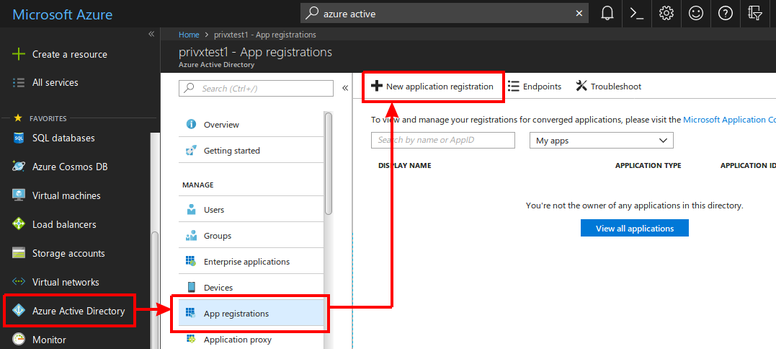
- Provide the following information regarding the PrivX app:
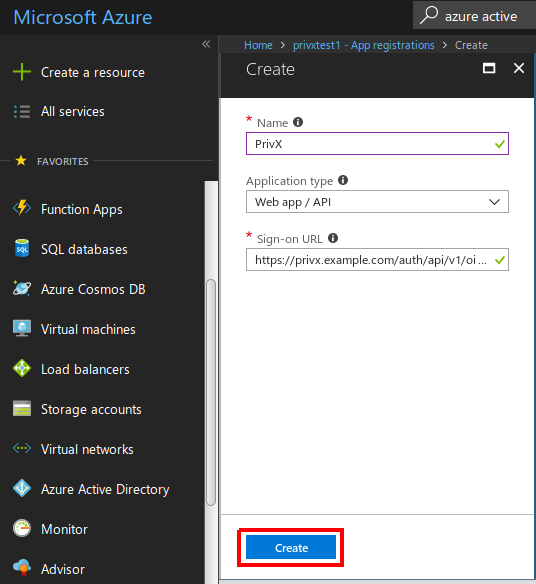
- Name: An arbitrary name for identifying the PrivX app.
- Application Type: Web app / API
- Sign-on URL: https:///auth/api/v1/oidc-cb (replace with the address of your PrivX server. Full working example: https://privx.example.com/auth/api/v1/oidc-cb)
- After providing the PrivX-app data, click Create.
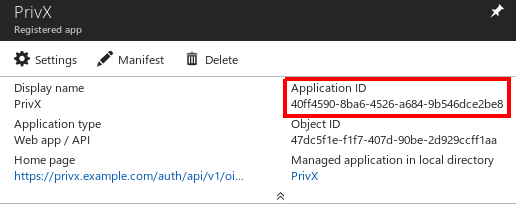
You should now see the details of your app. Copy the Application ID, which is later required for configuring PrivX.
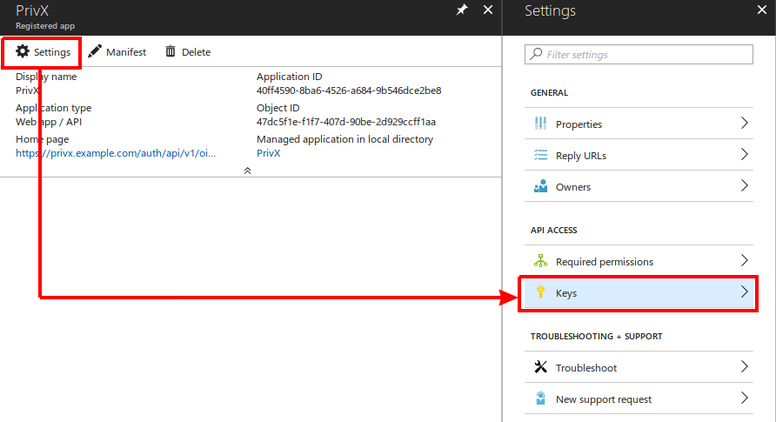
- Next, create an authentication key for the PrivX app. To do this, click Settings, then click Keys.
Enter the details for your key, then click Save.
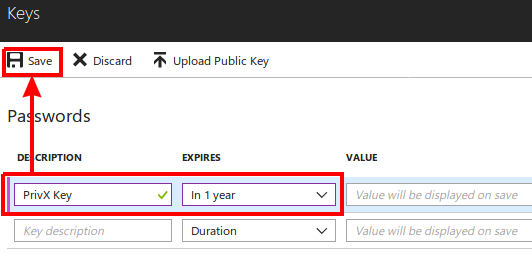
Copy the Value of the key, which is later required for PrivX configuration.
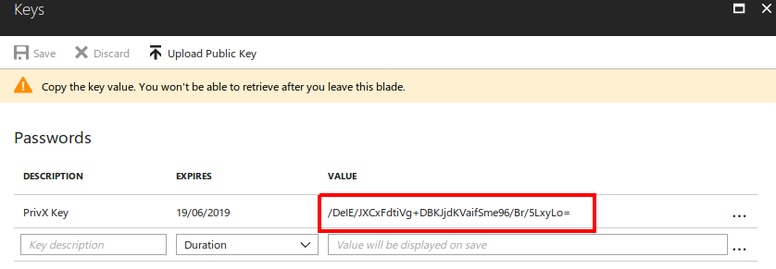
You have now successfully registered PrivX as an app in Azure.
Adding Azure AD users to PrivX
To allow LDAPS connections to Azure AD, the root-CA certificate of your Azure domain must be added as a trusted Certificate Authority (trusted CA). To do this, perform the following on each PrivX server:
- Gain root-terminal access to your PrivX server.
- Copy the root-CA certificate
After you have set up the root-CA certificate, configure PrivX to import users from Azure AD, and to authenticate Azure-AD users using Microsoft login:
- Access the PrivX GUI.
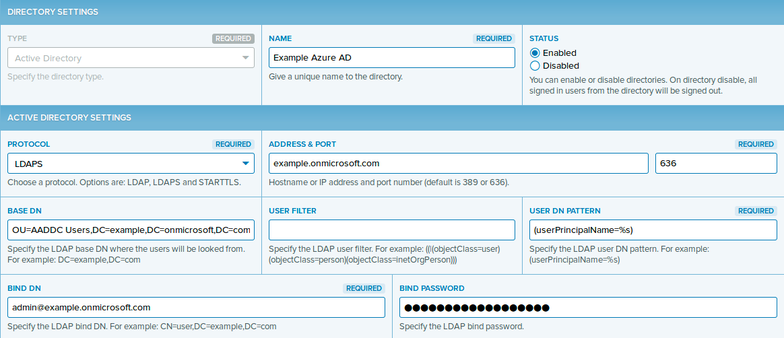
- On the Settings→Directories page, click Add Directory.
Add a directory of type Active Directory. Also set the connection protocol to LDAPS. Provide the rest of the required Active Directory Settings similarly to the following.
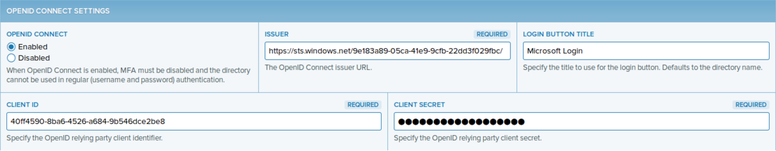
To enable Microsoft login (using the OpenID Connect standard), also provide the OpenID Connect Settings:
- OpenID Connect: Set to Enabled.
- Issuer: OpenID Connect Issuer URL, typically of the syntax (Replace with the Directory ID of your Azure AD):
https://sts.windows.net// - Login Button Title: An arbitrary name for the login button displayed on the PrivX login page.
- Client ID: The Application ID of the PrivX app.
- Client Secret: The value of a key in the PrivX app.
- Click Save to apply your changes. You should verify the directory back on the Settings→Directories page.
Note
It will take a while for PrivX to fetch and display the directory status. You should ensure that the directory status displays one or more users.
Verifying integration
You may verify integration by testing login with one of the Azure AD users:
- Log out from PrivX (if logged in). Navigate to the PrivX login page.
- Click the login button for your Azure AD. In this example, Microsoft Login.
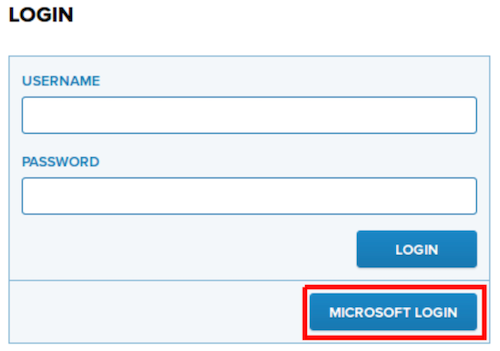
- Sign in with your Azure AD credentials.
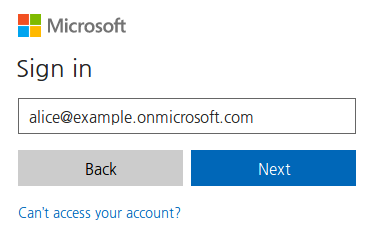
After successful sign in you will be logged into the PrivX GUI. Integration is now complete.
Updated over 3 years ago
