Configuring assume-role access to AWS API
PrivX Authentication to AWS Services via assume-role
This first example tells you how to configure PrivX to fetch temporary AWS API credentials via assume-role. Assume role credential validity period can be configured between 15 minutes and 12 hours (AWS restriction).
Values greater than 1 hour need to be configured in AWS target role settings:
Set up AWS users and roles for delegating AWS-service permissions, then grant these roles to PrivX users:
-
In your AWS management interface, create an IAM user for obtaining AWS roles.
Provide the IAM user with the following permission policies:{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": [ "*" ] } ] }You can further restrict the access by defining the target account role ARN as allowed resource:
"Resource": [ "arn:aws:iam::****:role/****" ]PrivX uses this AWS user to import and delegate AWS roles. For this reason you must also create Security Credentials/Access Keys for the user. Copy the Access Key ID and the Secret Access Key of the user, which are required later for configuring PrivX AWS Directory.
-
In your AWS management interface, create AWS role(s) that grant access to AWS services. This role does not need to be in the same AWS account, it can also belong to a third party.
The AWS role(s) should have permissions like the following (replace the example Actions with services and actions this role should allow access to).:{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "ec2:Describe*", "iam:ListRoles" ], "Resource": [ "*" ] } ] }ec2:Describe* -IAM permissions are required for AWS host scanning.
iam:ListRoles -permission is required by PrivX for role federation, for fetching a list of AWS roles for administrator to map PrivX roles against.
Also set the trust relationships of the AWS role similar to the following (replace <iam_user_arn> with the ARN of the previously-created IAM user):
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "<iam_user_arn>"
},
"Action": "sts:AssumeRole",
"Condition": {}
}
]
}
This allows PrivX AWS user to take control of this role to do host scanning or to get AWS API temporary credentials.
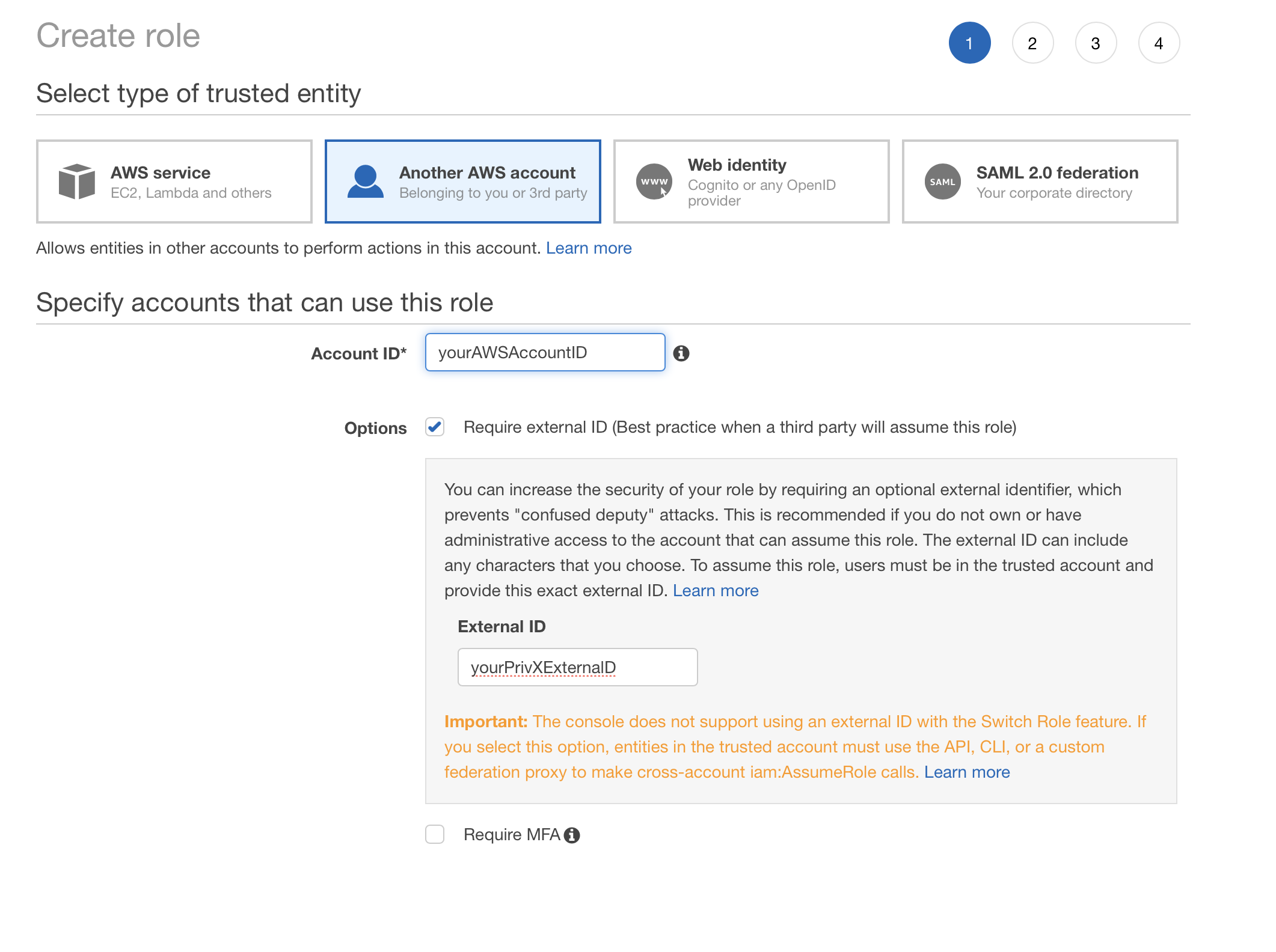
You can also grant the assume-role permissions via Create role wizard in AWS console,. although you need to modify the settings afterwards to include more externalIDs:
Note
To allow PrivX Agent users to assume the role via PrivX, the AWS role must have a unique Name tag.
Place PrivX-specific roles under a unique path (such as /privx/). PrivX can be configured to import roles from this path, ignoring irrelevant roles in your AWS environment.
Configuring PrivX AWS directory to use role federation
-
On the Settings→Directories page of the PrivX GUI, add a directory of the type Amazon Web Services. Provide the Access key ID and Secret Access Key of the previously-created IAM user.
Also under Advanced AWS settings, select Enable AWS Role Federation. If you only want to import roles under a certain path, set this path to AWS Role Prefix for Federated Roles.
Save the directory configuration. To verify that roles were imported successfully, ensure that the previously-configured AWS roles are visible on the page Settings→Deployment→Configure Amazon Web Service role grants. -
Grant AWS roles to PrivX roles. To do this, go to the page Settings→Deployment→Configure Amazon Web Service role grants, and Edit the AWS roles. PrivX users belonging to specified roles can now gain access according to any AWS roles granted to them.
Updated over 3 years ago
